Big data and Internet technologies are expected to play an important role for the implementation of a human and affordable health system. However, humans have to be in focus when designing the technology and its use. A decentralized approach and digital sovereignty of users are decisive qualities of the planned technology investments. We are all responsible for requesting and promoting these design criteria for the use of Internet technologies in our health system.
- Details
- Written by Manfred Reitenspiess
Read more: The Right Internet Technologies for Our Health System
At CES 2016 in Las Vegas we could see a number of new offerings around payment systems. They are all based on Internet technologies and mostly use one or more smartphone features and apps. But what about alternatives which are convenient and secure and even anonymous?
- Details
- Written by Manfred Reitenspiess
Our digital alter ego is abundant - and we better take care of it. The concept of digital sovereignty should help us to manage it.
Each and every one of us has a digital alter ego. But who of us knows, where this alter ego is stored? Even more relevant: which attributes are associated with our alter ego? Or: who is making money from knowing or using our alter ego? May be only partially or in combination with other data? Digital sovereignty – the management or control of our alter ego in the digital world – should help us answer above questions when managing our digital alter ego.
- Details
- Written by Manfred Reitenspiess
Digital sovereignty denotes the authority of individuals over their presence and representations in the digital world.
The definition of digital sovereinty is relatively flurry due to its varying meanings. So for this brief discussion, we have searched for both: digital sovereignty and data sovereignty. What we found was that the terms' interpretations take mainly a governmental view based on definitions for "sovereignty" (different from the terms' use in Germany as discussed in Digitale Souveränität - Was ist das?).
- Details
- Written by Manfred Reitenspiess
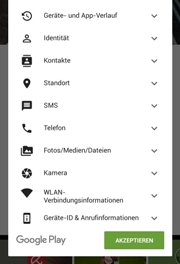
It is so easy - everything is for free, just check out the Internet! Click on a free App, download the App, install and run. One can find Apps for nearly everything. And for even the simplest pieces of information you give away whatever is stored about you on your phone. The image shows a quick example what you open up when installing a virus scan tool (I have checked at least 5 of them and only one out of 5 had a reduced set of requirements).
- Details
- Written by Manfred Reitenspiess
Think about it - the Internet has grown from a tool of a bunch of nerds into a world-wide available infrastructure, which is used by billions of people, on a professional as well as on personel level.
For each item in the real world, we all profit from a legal framework which allows us to move (more or less) safely about. But what about the digital world? To me this looks much more like Wild West than anything else. In many ways we depend upon the goodwill of international players who confront us with usage regulations 20 pages long before allowing us to use our smartphone which we have paid for!
- Details
- Written by Manfred Reitenspiess
Page 2 of 2